ShadowServer has discovered more than 17,000 Fortinet SSL VPNs compromised by what’s known as the symlink backdoor. We obtained the remote detection method from a trusted source and integrated it into our external attack surface management solution. Explanations.
Where does this backdoor come from?
On April 10th 2025, Fortinet revealed that SSL-VPN devices had been compromised via the exploitation of known vulnerabilities dating back to at least 2023. Vulnerabilities CVE-2022-42475, CVE-2023-27997, and CVE-2024-21762 were reportedly exploited to deploy a persistence mechanism on the compromised devices.
This mechanism allows an attacker to maintain remote access to the machine, even after the system has been updated with security patches.
How to detect it remotely?
To put an end to the suspense, we will not be revealing the detection method publicly. Indeed, it could allow anyone to take control of impacted systems, and we do not want to arm cybercriminals.
However, we believe this detection method should be shared with organizations (commercial or not commercial) that wish to use it. Any organization working to protect businesses against intrusions should have access to this method. We firmly believe that this type of information must be shared, not kept within a small circle, so that together we can fight cybercrime. Only by joining forces will we have a chance of winning.
That’s why we are willing to share it, privately, with organizations that have a track record showing they are working for cyber defense. This includes our competitors. We call on all these stakeholders to privately share methods and techniques that prevent intrusions from the Internet, or methods allowing to alert a vulnerable (or compromised) entity.
Number of compromised machines
The total number of compromised machines on April 22nd 2025 is:
- Near 22,000 devices
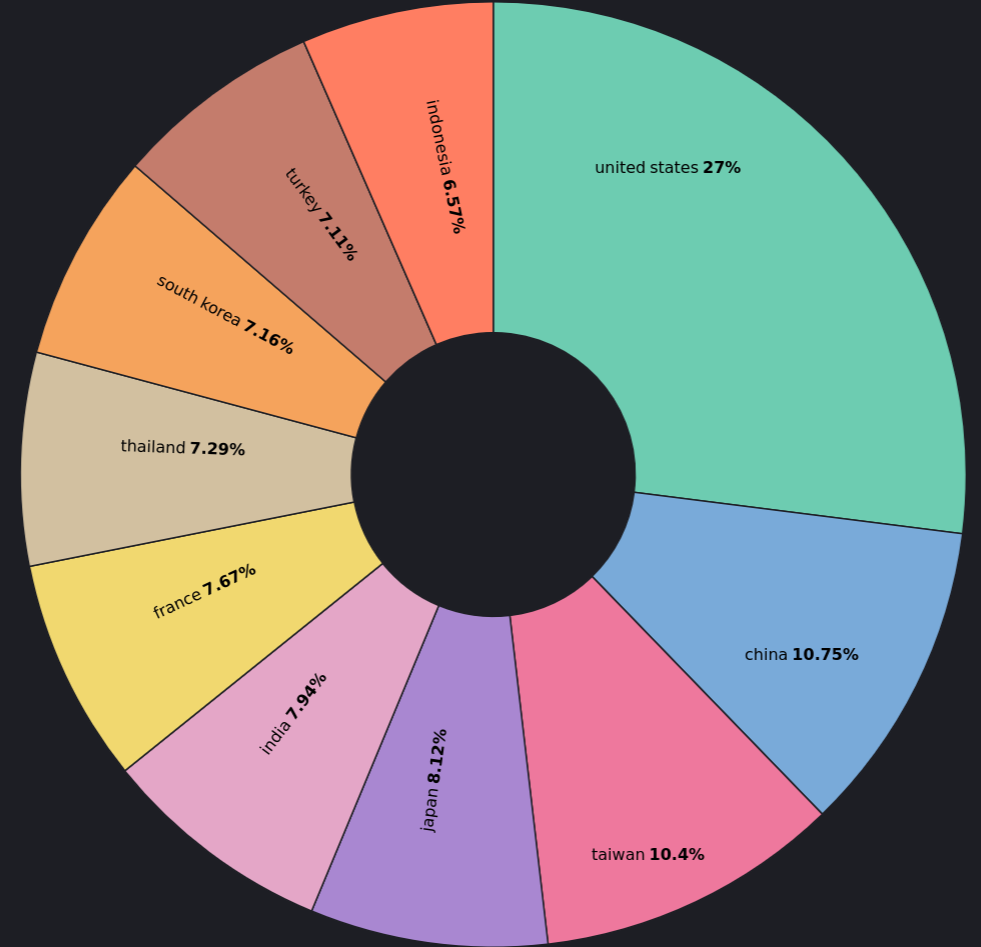
Geographic distribution of the TOP 10 most affected countries:
Conclusion
If you are an organization, whether for-profit or not, whether a competitor of ONYPHE or not, you can contact us via our email address: contact at onyphe.io. If we believe you are working to protect against cybercrime, we will provide you with remote detection details.
If you are a victim of this backdoor, we recommend reading the Fortinet article on the appropriate cleanup methodology.

