Orange Cyberdefense (OCD) has discovered a critical vulnerability (CVE-2025-32432) in the Craft CMS software. OCD has approached us to work in partnership to identify the number of vulnerable machines on the Internet. This post provides essential information about this CVE.
Is this flaw really critical?
Yes. It’s as simple as that. This is a remote, unauthenticated execution of arbitrary code. The CVSS score is 9.8, even though, as we regularly repeat, at ONYPHE, we do not look at CVSS scores.
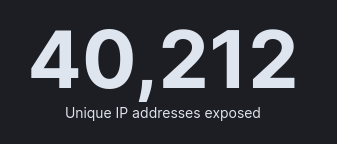
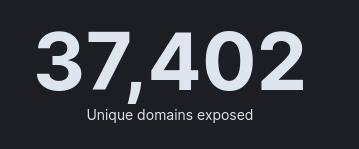
Additionally, it’s a widely exposed product on the Internet because it allows content to be published. Many companies use it. According to our data, more than 40,000 IP addresses representing over 37,000 domain names expose this software on the Internet.
All our red flags regarding our vulnerability criticality classification method are here:
- Remotely exploitable
- No authentication
- Arbitrary code execution or authentication creds data leak
- Widely used product
- By large companies
Our score, which is binary, therefore rates this CVE: 1. This vulnerability will be exploited and cause damage.
The scoring system we use to determine whether we should add a detection method to our attack surface management solution is very simple:
- Check all the boxes described above
- Yes: the score is 1
- No: the score is 0
- If our highly predictive scoring fails, the news shows it being exploited, and the flaw is then seen being exploited “in the wild“, we increase the score to 1 and add it to our solution.
Furthermore, in order to add the detection to our engine, we must be able to check the vulnerability in non-intrusive ways only. We abide by French laws. Thus, not all score 1 issues can be assessed by our solution.
However, we must point out that ONYPHE is not a vulnerability scanner. We only seek to identify the vulnerabilities actually exploited by cybercriminals. For all other useless vulnerabilities, there are numerous vulnerability management products or SaaS solutions.
Is there a PoC?
Yes, there is a PoC. Just read by OCD blog post to find out more.
Also, according to the publisher, it’s already being exploited “in the wild”:

OCD/ONYPHE partnership
OCD contacted us after their teams discovered this CVE. They wanted a list of machines exposing this CMS to the internet. We worked with them, providing them with the requested information so they could, in turn, assess the number of vulnerable machines.
We’ve done the same. For our customers, identifying vulnerable Craft CMS is now integrated into our attack surface management solution.
Number of vulnerable machines
The total number of vulnerable machines as of April 20th, 2025, was:
- 8,137 unique IP addresses representing:
- 12,168 unique domains
- 15,093 unique FQDNs
We can clearly see shared IP addresses hosting multiple domain names. ONYPHE is able to detect this because we also scan full URLs, i.e., using Virtual Host via the HTTP Host header.
Any attack surface management solutions that don’t scan URLs risk missing vulnerable machines…
Conclusion
If you use this product, patch it. Fast. These days, cybercriminals exploit new vulnerabilities within 24 hours.

